

As someone who sends emails, you’ve probably heard about the importance of following email best practices to get the best results from your email program. One of these best practices is ensuring that you properly authenticate your email messages. However, understanding the three pillars of email authentication – SPF, DKIM, and DMARC – can be challenging, especially with all the email acronyms out there. So let’s take a closer look at these components of email authentication and why they are so crucial.
Authentication refers to the process of proving or showing something to be true, genuine, or valid. When it comes to email, authentication involves SPF, DKIM, and DMARC. These tools provide evidence that an email message is genuine and originates from the claimed sender.
But why does email authentication matter? Well, given the abundance of spam and phishing messages in the email world, it’s even more important that your messages are properly authenticated. Email authentication serves as your digital ID card and helps Mailbox Providers (MBPs) and spam filtering systems recognize your legitimate emails.
The two primary authentication protocols that validate the sender’s identity in an email message are SPF and DKIM. And on top of that, there’s DMARC, which uses SPF and DKIM and provides a set of instructions to receiving email servers on what to do if they receive unauthenticated emails.
Now that you have a general understanding of these three valuable email authentication tools, let’s delve into how each component works.
An example how to look in CloudFlare:
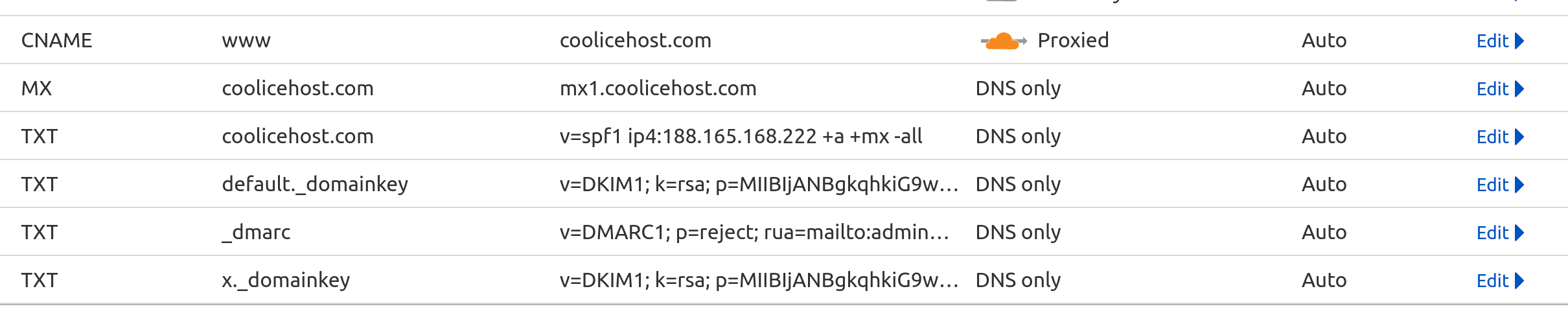
You can visit the documentation on Set up email records in CloudFlare
What Is Sender Policy Framework (SPF)?
Sender Policy Framework (SPF) is an authentication protocol that confirms the authorized IP addresses allowed to send emails on behalf of domains. When you send an email, the recipient’s system checks for the presence of an SPF record. If a valid SPF record exists and your sending IP is included in the list, your email passes the SPF check. On the other hand, if your IP is not listed, your email fails the SPF check and may be rejected or directed to the spam folder.
A typical SPF record looks like this:
domain.com. – 3600 – TXT – “v=spf1 a mx ip4:5.196.35.199 ~all”
However, SPF authentication has some limitations when it comes to validating the source of a message. Additionally, SPF is unable to protect brands against individuals who can impersonate the display name or friendly-from address. These limitations are among the reasons why DKIM was developed.
SPF and DKIM are both important email authentication methods. Another vital method is DMARC. By implementing DMARC, domain owners can specify their preferred email authentication mechanisms (SPF, DKIM, or both) and instruct receiving systems on how to handle any failed authentication attempts. This helps combat phishing attacks and ensures the security of email communications.
What is Domainkeys Identified Mail (DKIM)?
Imagine SPF, DKIM, and DMARC as tools that ensure the security and authenticity of your emails. SPF, or Sender Policy Framework, helps verify that the server sending the email is authorized to do so on behalf of the domain. DKIM, or DomainKeys Identified Mail, adds a digital signature to each email, allowing the receiving server to validate the sender’s identity and check if the email has been tampered with during transmission.
Both SPF and DKIM assist Mailbox Providers (MBPs) in filtering emails and deciding whether they should be delivered to the inbox, marked as spam, or rejected. However, these authentication methods do not enable domain owners to instruct MBPs on how to handle unauthenticated emails.
To address this issue, DMARC, or Domain-based Message Authentication, Reporting, and Conformance, combines SPF and DKIM and allows domain owners to provide instructions on how to treat unauthenticated emails. It helps MBPs make informed decisions about whether to deliver, quarantine, or reject such emails.
By implementing SPF, DKIM, and DMARC, you can enhance the security of your emails, protect against spoofing, and ensure that your messages are delivered to the intended recipients.
How DKIM Works
In a nutshell, DKIM uses asynchronous encryption and can work with any tool designed for this purpose. The first step is to generate a private/public key pair for your business. The public component of this key should be added as a TXT record associated with the sender domain. The private key is then used to create a DKIM-Signature for each outgoing email. This signature is essentially a hash code created by combining the email content with the private key using a security algorithm. The DKIM-Signature is then added as a header to the email.
When a receiving SMTP server detects this header, it looks up the public key through the domain name system (DNS) by requesting the specific TXT record. The advantage of asynchronous encryption is that the keys have shared data DNA in a sense. The public key allows anyone to verify if the email was indeed sent by the domain owner, thus ensuring the legitimacy of the message. If this verification fails or the header/signature is missing, most email service providers will flag the email. Depending on the amount of email sent, the provider may classify it as spam or even block the sender’s IP address. To avoid these issues and ensure delivery, it is crucial for your company email to have DKIM configured. This will also enhance your brand’s reputation.
How to Set Up DKIM
To set up DKIM, follow these main steps:
1. Configure DKIM to Generate the Key Pair: The tools needed for this process depend on your operating system. Contact MxToolbox for guidance tailored to your situation.
2. Create the Public Key as a TXT Record in DNS Settings: Update the settings of your chosen DNS provider accordingly. Note that some providers may be more challenging to navigate, but MxToolbox is here to assist you.
3. Generate and Save the DKIM-Signature: Apply a unique signature to your messages to ensure successful email delivery.
If your company sends messages through third-party providers, DKIM setup is required for each provider. Make sure all your outbound domains apply this protocol. MxToolbox makes it easy to implement DKIM for your business. Let us know how we can help you achieve 100% DKIM, SPF, and DMARC compliance.
You can take a loot at these tools:
It usually this record looks like this:
x._domainkey – 3600 – TXT – “v=DKIM1; k=rsa; p=MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA0AQkYGhEIbXHf3p0lCDz2hkrpo4muKKq7NbteE0chlsw42bddu4imCIgdXZRrjw3OBKKTIfPHxToasHft3ZwzMbKaTfTZtJUXRsG+5adh8vB9ESpw4D2wYg2zeVlJyX6mxisM7vbVs82iXFd0PUzLW5hYSEuH8ZX46rZTzhUpbU9ERSSP6FwQBWJBE0zns7UYM7yZHsoyQExdTxaHuM1PY4p9i4smx0gYrHknax83iX3utfNdtlX6vYCaXZqhSJ+2H6PfHBGELMVaqGL07RxHK5GTtNi5eljvw1kF9RLvNgvBxs5N96AIlZcldDVr+LmxiwxOfbOg28LMSRXCW1JPwIDAQAB”
What is Domain-based Message Authentication, Reporting & Conformance (DMARC)?
Our third authentication component is called Domain-based Message Authentication, Reporting & Conformance (DMARC). It is a protocol for authenticating emails and setting policies for how unauthenticated messages should be handled. DMARC helps prevent domain spoofing and phishing attacks by preventing unauthorized use of the domain in the Friendly-From address of email messages.
With DMARC, the domain owner can specify how unauthenticated messages should be treated by Mailbox Providers (MBPs). This is done through a “policy” that is set in the DMARC DNS record. There are three options for the policy: NONE, QUARANTINE, and REJECT.
– If the policy is set to “NONE,” no action is taken and the message is delivered as normal.
– If the policy is set to “QUARANTINE,” the message is placed in the spam/junk/quarantine folder.
– If the policy is set to “REJECT,” the message is rejected/bounced.
The “R” in DMARC stands for the Reporting component of the protocol. DMARC allows the domain owner to receive reports that show where all emails using their domain in the From address are being sent from.
To summarize, SPF, DKIM, and DMARC are authentication components that help ensure the security and authenticity of email messages. DMARC specifically addresses domain spoofing and phishing attacks by allowing domain owners to set policies for handling unauthenticated messages. The reporting feature of DMARC provides valuable insights into the use of the domain in email addresses.
Are you wondering how to begin with SPF, DKIM, and DMARC? Let’s explore the basics of these important keywords!
To begin configuring SPF, DKIM, and DMARC, start by contacting your support team to check if you have already implemented email authentication. If not, they will provide the necessary documentation to assist you in setting up the appropriate authentication for your platform. If you have already done so, you can mark that task as completed!
Enabling email authentication is not only a recommended best practice for delivering emails successfully, but it also plays a crucial role in safeguarding your brand’s reputation. By limiting the chances of unauthorized senders using your domain without permission or knowledge, these authentication tools help protect your brand’s integrity.
Remember, reaching out to your support team is the first step towards ensuring the effectiveness of SPF, DKIM, and DMARC in securing your email communications.






