Home »
Archive by category Hosting Industry
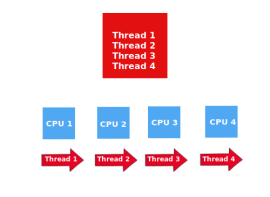
What exactly is a CPU? A server’s central processing unit (CPU) is a physical component that houses the main computing unit. Data is transformed into digital signals by servers and other smart devices, which then use those signals to do mathematical operations. The main element that processes the...
Continue reading
March 20, 2024 admin
Hosting Industry
No Comment
Introduction Are you a small to medium business owner concerned about the security of your online business but overwhelmed by technical jargon? You are not alone. Ensuring the security of your online presence and reputation is important, but it doesn’t have to be complicated. This to-do list is...
Continue reading
March 5, 2024 admin
Hosting Industry
No Comment
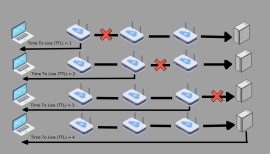
What does networking’s time-to-live (TTL) mean? The term “time to live” (TTL) describes the number of “hops” that a packet is allowed to stay in a network before a router discards it. TTL is also utilized in other settings, such as DNS and CDN caching. How does TTL...
Continue reading
February 13, 2024 admin
Hosting Industry
No Comment
With the help of this useful set of commands, monitor disk consumption. One of the everyday tasks for system administrators (and others) is to monitor disk utilization information. A few built-in tools in Linux assist in providing that information. The df command in Linux The Linux program df,...
Continue reading
January 29, 2024 admin
Hosting Industry
No Comment
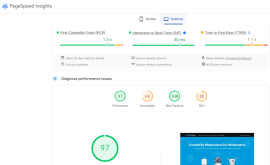
When it comes to the performance of websites, web administrators and SEOs frequently have two questions that may be answered by internet tools: What is the speed of my website? How can I make my website performs better? Numerous website-monitoring solutions are available to find these issues if...
Continue reading
January 19, 2024 admin
Hosting Industry
No Comment
Brief introduction Website owners and SEO experts should prioritize the goal of decreasing server response time. It is a pointless investment of resources to create a website if it takes too long to load and drives visitors away. The initial few seconds are crucial in determining whether a...
Continue reading
November 27, 2023 admin
Hosting Industry
No Comment
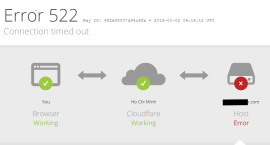
The Cloudflare error 522 is an error code that means a server is unable to reach a specific webpage. It is also known as the connection timeout error. In this article, we will explain what this error is, why it happens, and provide solutions to fix the Cloudflare...
Continue reading
September 11, 2023 admin
Hosting Industry
No Comment
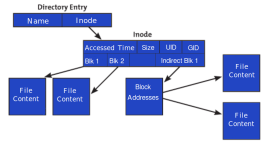
An inode represents every single file, directory and symlink in the hosting account. An inode (index node) is a fundamental concept in the Linux/UNIX file system. Each object in the file system is represented by an Inode. What is Inode? Every file in a Linux/UNIX environment has the...
Continue reading
September 4, 2023 admin
Hosting Industry
No Comment
Hello! Today we will share some important and basic stuff you need to know in order to: Setup your hosting account properly Run it with no problems Manage it the right way. We publish it here in order to decrease the number of tickets you are about to...
Continue reading
August 29, 2023 admin
About CooliceHost, Hosting Industry
No Comment
In this post, we will be exploring the difference main between normal and jailed shell, and what the terms stands for. What is Normal Shell? This option can grant the user access to the shell with no limitations. What is Jailed Shell? This option can grant the user...
Continue reading
August 11, 2023 admin
Hosting Industry
No Comment